DDoS Protection
- ICN monitors and detects DDoS attacks * ICN notifies the customer during or after the attack and mitigates upon customer request
- ICN provides information on the attack upon request
- Mitigation scrubs incoming traffic and attempts to provide only the good packets to the customer
- ICN may black hole the IP address under attack
- ICN automatically mitigates the attack (given customer approval) * 10G+ Mitigation via both State-wide and global cloud based DDoS Mitigation system
- Mitigation scrubs incoming traffic and attempts to provide only the good packets to the customer
24/7 Customer traffic monitoring by ICN Network Operations Center
Tier 1 Network Engineers on hand at the NOC at all times. Attack Monitoring
Monitoring customer traffic identifying and mitigating attacks in their infancy
Use of advanced heuristics to profile normal versus anomalous traffic patterns
Specific points or asset protection within a customer's network (such as existing firewalls, gateways, webservers, DNS servers, etc)
Always-on monitoring - Flow or signals based
Detailed and unified event reporting for multiple environments through a secure portal ** Threat Detection
Customer-specific alerts enabling trained security experts to immediately identify nascent potential attacks
Signature analysis
Misuse detection
Predefined deviations recognition
Dynamic Profiling
Normal traffic baselining
Requires no customer premise equipment Mitigation
On-demand mitigation
On-Ramping Traffic (e.g. BGP announcements)
Use of filtering (state-of the-art filtering technology to increase the level of filtering to progressively block more malicious traffic or more sophisticated attacks)
Off-Ramping Traffic (once traffic is "cleaned," redirecting it back to the customer's network)
Scalable mitigation solution *Auto-Mitigation *
ICN will automatically mitigate the attack (with customer permission) based on a baseline of the customer’s bandwidth usage pattern
Customers have access to review their data via a custom network monitoring portal, and to generate their own reports, dashboard, etc.
Custom Reporting
Traffic summary reports
Application reports
Protocol reports and event reports
Fingerprints reports
Transit research
IP header reports
BGP reports
- TCP loss reports
QoS and Services reports
Traffic with other customers
Top Talkers reports
Description
The Distributed Denial of Service (DDoS) mitigation service reduces or removes the impact of DDoS attacks against customer infrastructure. A distributed denial-of-service (DDoS) attack is an attempt to make an online service, website or network unavailable by overwhelming it with traffic, stopping even legitimate traffic.
Service Levels
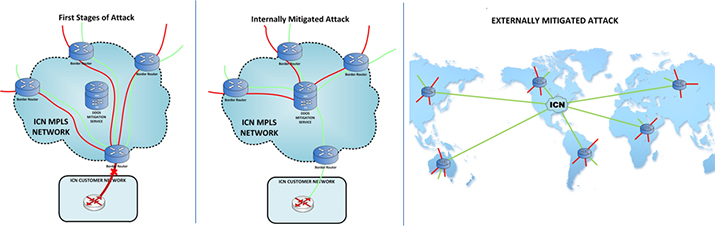
Standard requires setup time, approval from customer and is implemented locally within ICN.
Advanced includes Standard services and allows for auto-mitigation and an ability to mitigate much larger attacks for longer periods of time utilizing a global, cloud-based service. Because of these features, Advanced provides customers with minimal disruption of network services during an attack.
Standard
Advanced
Includes Standard features, plus
Optional
The following Services are available to Advanced DDoS Mitigation Customers at an additional price as detailed in the Rates table, below:
DDoS Dashboard: ICN sets up a Peakflow page for customers to view their managed object and the attacks and receive automatic notifications.
*DDoS Incident Reporting: *Custom Reporting is available upon request. Report types are identified in the Optional Features table provided below under "Custom Reporting".
DDoS Consultation: ICN provides consultation on how to reduce impact of DDoS attacks on customer network.
Features
24/7 NOC
Optional Features
DDoS Dashboard
Questions about DDoS Services?
Complete the form below, or contact your Regional Technology Center for service order information and support.

